Department of Defense Issues Final Rule to Implement Cybersecurity Maturity Model Certification (CMMC) Program
After more than six years of deliberations, significant revisions, and volumes of commentary from defense contractors, the Department of Defense (DoD) has finalized its Cybersecurity Maturity Model Certification (CMMC) program. On September 9, 2025, the DoD issued its final rule amending the Defense Federal Acquisition Regulation Supplement (DFARS) to incorporate CMMC requirements into defense contracts (the Acquisition Rule). DoD finalized a separate rule containing most of CMMC's substantive requirements in 2024 (the Program Rule).
The core cybersecurity requirements underlying CMMC have been part of the DFARS and government contracts for nearly nine years. In 2016, DoD amended the DFARS to require contractors to protect Covered Defense Information (CDI), including by notifying DoD of data breaches and to comply with the requirements of National Institute of Standards and Technology (NIST) Special Publication 800-171 Revision 2 (NIST SP 800-171). Under CMMC, contractors now must obtain certifications that they comply with those (and in some cases, additional) cybersecurity requirements. DoD developed CMMC in part out of a concern that many defense prime contractors and subcontractors still are noncompliant the DFARS security requirements.
The Acquisition Rule becomes effective on November 10, 2025. Thereafter, DoD will begin to introduce CMMC certification requirements in a phased implementation approach, with full program implementation by November 10, 2028. Once these requirements are in place, contractors will not be able to obtain a DoD contract unless they have achieved the applicable CMMC certification level. The DoD estimates that hundreds of thousands of entities may need to undergo some type of assessments under CMMC within the next 10 years.
We provide a brief history and overview of the CMMC program and identify important considerations for defense contractors.
A Brief History of CMMC
DoD first announced its intention to create the CMMC program in 2019. In September 2020, DoD published an interim CMMC rule establishing an "assessment methodology" for contractors' compliance with NIST 800-171 and certain other cybersecurity requirements. That framework included five certification "levels," with each level requiring a contractor to demonstrate its compliance with an increasingly broad set of cybersecurity requirements. Cybersecurity requirements for defense contractors, including compliance with NIST SP 800-171, already were in the DFARS—and therefore in DoD solicitations and contracts—but the DFARS did not provide any method for DoD to verify contractors' compliance with those requirements.
In November 2021, DoD issued an advanced notice of proposed rulemaking (ANPRM) announcing a significant overhaul of CMMC, dubbed "CMMC 2.0." DoD explained in the ANPRM that it had decided to make substantial changes to CMMC based on an internal review of the program that was "informed by more than 850 comments" to the proposed CMMC rule. We discussed CMMC 2.0 in detail in a 2021 post. CMMC 2.0 reduced CMMC's five certification levels to three, more closely aligned some required cybersecurity practices to existing NIST standards, and—perhaps most importantly for contractors—permitted certain lower-risk contractors to self-certify their compliance. Previously, all contractors subject to CMMC would have been required to undergo assessments by the DoD or an accredited CMMC Third Party Assessment Organization (C3PAO). DoD proposed the Program Rule to establish CMMC 2.0 in December 2023. In August 2024, DoD proposed the Acquisition Rule to incorporate CMMC requirements into the DFARS.
In October 2024, DoD issued the final Program Rule amending 32 C.F.R. Part 170. That rule formally established the program's structure, assessment levels, and phase implementation, in line with CMMC 2.0. As a final step in this lengthy process, DoD issued the final Acquisition Rule on September 10.
Overview of Key CMMC Requirements
CMMC applies to DoD contractors that "process, store, or transmit" either Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) on contractor information systems. FCI is a broad term and is defined in the Federal Acquisition Regulation (FAR) as "information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government…." CUI is a more complex concept, defined in federal regulations as "information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls." Covered Defense Information or CDI, referenced in the DFARS cybersecurity requirements, is a subset of CUI specifically related to defense contracts. CMMC does not apply where a contractor operates a government information system on the government's behalf. CMMC also does not apply to commercial-off-the-shelf (COTS) products.
CMMC applies to both DoD prime contractors and subcontractors. Under the Program Rule, prime contractors must flow down CMMC's certification requirements to any subcontractor that "processes, stores, or transmits" FCI or CUI.
In line with the CMMC 2.0 overhaul, CMMC will require defense contractors to undergo one of three certification "levels" to obtain a defense contract. The level a contractor will obtain depends on the level specified in the solicitation, which is dictated by the types of DoD information the contractor would handle. CMMC's three certification levels are:
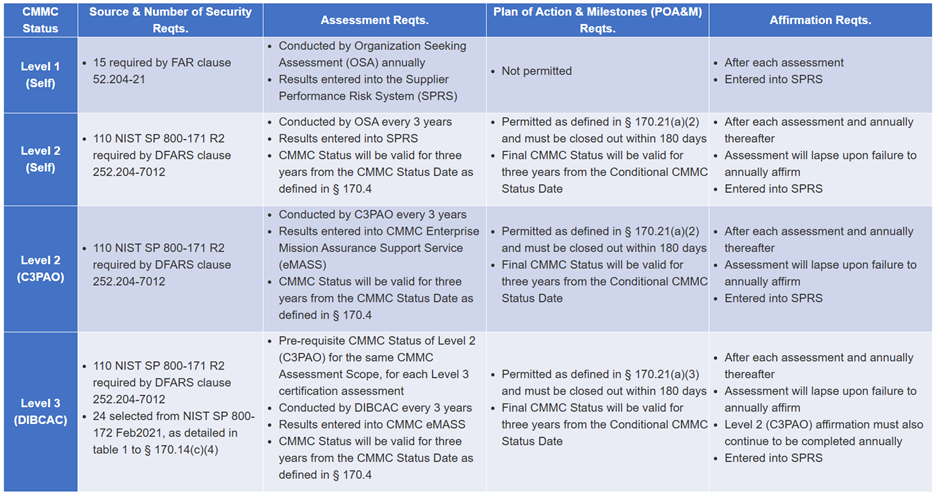
- Level 1: Basic Safeguarding of Federal Contract Information (FCI). Requirements include an annual self-assessment and annual affirmation of compliance with 15 security requirements in FAR 52.204-21, as well as any other specific safeguarding requirements that may be specified by Federal agencies. At Level 1, contractors need not certify their compliance with NIST SP 800-171.
- Level 2: Broad Protection of CUI. Requirements include either a self-assessment or a (C3PAO) assessment every three years, depending on the type of information processed, transmitted, or stored on the contractor or subcontractor information systems. Contractors must annually verify their compliance with the 110 security requirements in NIST SP 800-171 Revision 2.
- Level 3: Higher-Level Protection of CUI Against Advanced Persistent Threats. In addition to the requirements of Level 2, contractors must undergo an assessment every three years by the Defense Contract Management Agency's Defense Industrial Base Cybersecurity Assessment Center (DIBCAC). Contractors must also provide an annual affirmation verifying compliance with the 24 identified requirements from NIST SP 800-172.
At each of these levels, a "senior official" from the contractor must "affirm continuing compliance" with the applicable security requirements. The DoD's Chief Information Officer (who heads the CMMC program) has provided this helpful chart outlining the various certification levels and requirements, copied below:
As referenced in the above chart, contractors pursuing CMMC certification at levels 2 and 3 may leverage a Plan of Action & Milestones (POA&M) to address noncompliance with certain CMMC requirements identified during an assessment. Use of a POA&M allows contractors to be out of compliance with those requirements for up to 180 days under a conditional status while they pursue remedial action to close out their POA&Ms. Contractors cannot use POA&Ms for Level 1 self-certifications.
Phased Implementation and Next Steps
Under the Program Rule, CMMC will roll out in four phases over three years based on the certification level applicable to a DoD solicitation. DoD intends to introduce self-assessment requirements under levels 1 and 2 beginning on November 10, 2025—the day the Acquisition Rule becomes effective. During that initial phase, DoD may implement Level 2 C3PAO assessments as well. One year later, DoD intends to begin introducing Level 2 C3PAO assessments, with discretion also to introduce Level 3 DIBCAC assessments. One year after that, DoD intends to introduce Level 3 DIBCAC assessment requirements. Note that DoD Contracting Officers have discretion to delay the inclusion of requirement for CMMC Status Level 2 and 3 to an option period instead of as a condition of contract award. All applicable DoD solicitations and contracts are to include all CMMC requirements by November 10, 2028.
The DoD's CIO also has provided this diagram of the CMMC phased rollout:

Although requirements to comply with NIST SP 800-171 have been in the DFARS for over nine years, many contractors have been scrambling to catch up to the CMMC program's requirements. One study released a year ago found that only four percent of DoD contractors were prepared to comply with CMMC at that time. Risks to contractors are significant. The Department of Justice (DOJ) has continued to pursue high-profile False Claims Act cases against defense contractors for allegedly falsely certifying their compliance with NIST SP 800-171 and other cybersecurity requirements, as part of DOJ's Civil Cyber-Fraud Initiative.
Contractors working towards CMMC compliance should considering the following steps:
- Determine your appropriate certification level and compliance scope. Contractors should assess the FCI and CUI that they or their subcontractors expect to process, store, or transmit as part of their defense contracts to determine their likely certification level and scope of their compliance obligations. CMMC assessments will be performed based on a defined "assessment boundary," including all assets that process FCI or CUI. Remember that under the final rule, offerors will be ineligible for award of a contract, task order, or delivery order if they do not have the results of a current CMMC status (including a conditional status and a POA&M, where available) entered in the DoD's Supplier Performance Risk System (SPRS) at the required CMMC level, as well as a current affirmation of continuous compliance for each of the contractor information systems that will process, store, or transmit FCI or CUI and be used in performance of an award. Contracting officers are required to check SPRS before awarding a contract to ensure all required information is present.
- Baseline against NIST SP 800-171 and CMMC requirements. To prepare for CMMC assessment, contractors should evaluate their cybersecurity practices against NIST SP 800-171 and the CMMC program requirements. Contractors should work expeditiously to resolve any gaps ahead of required assessments, taking into account the phased rollout approach and noting that DoD has discretion to introduce some assessments early.
- Consider Subcontractors When Assessing Compliance. Keep in mind that CMMC requirements apply to subcontractors throughout the supply chain at all tiers that will process, store, or transmit any FCI or CUI on contractor information systems in the performance of a DoD contract or subcontract. It is incumbent upon prime contractors to ensure that subcontractors comply with and flow down CMMC requirements. Prior to submitting any proposal or offer, prime contractors should consider whether subcontractors will process, store or transmit FCI or CUI. Note that under the final rule, the subcontract flowdown language in the clause was updated to identify that subcontractors also must submit affirmations of continuous compliance and the results of self-assessments in SPRS.
- Address external service providers (ESPs). Contractors should review their contracts with ESPs, including managed service providers and cloud service providers. Contractors are permitted to use cloud services that either have achieved a "Moderate" (or higher) baseline under the Federal Risk Authorization and Management Program (FedRAMP), a cybersecurity assessment and authorization program for cloud service offerings, or that meet "equivalent" security requirements under DoD policy. Systems and services provided to contractors by ESPs are subject to CMMC assessments and must be documented in the contractor's Systems Security Plan (SSP).
- Consult DoD guidance. The DoD's CIO has published numerous guides, FAQs, and fact sheets to help prime contractors and subcontractors understand and comply with CMMC. Many of those resources are consolidated here: DoD CMMC Resources & Documentation.
Conclusion
Although the core technical requirements underlying CMMC have been in the DFARS for years, CMMC will soon require prime contractors and defense contractors to the DoD to undergo self or third-party assessments to certify their compliance those (and in some cases, additional) requirements. Organizations that intend to receive DoD contracts should assess whether they will need CMMC certification, and if so, at which certification levels.
DWT's privacy and security and government contracts teams will continue to monitor developments with CMMC.